二進制
docs/modules/ROOT/assets/images/servlet/exploits/csrf-processing.odg
二進制
docs/modules/ROOT/assets/images/servlet/exploits/csrf-processing.png
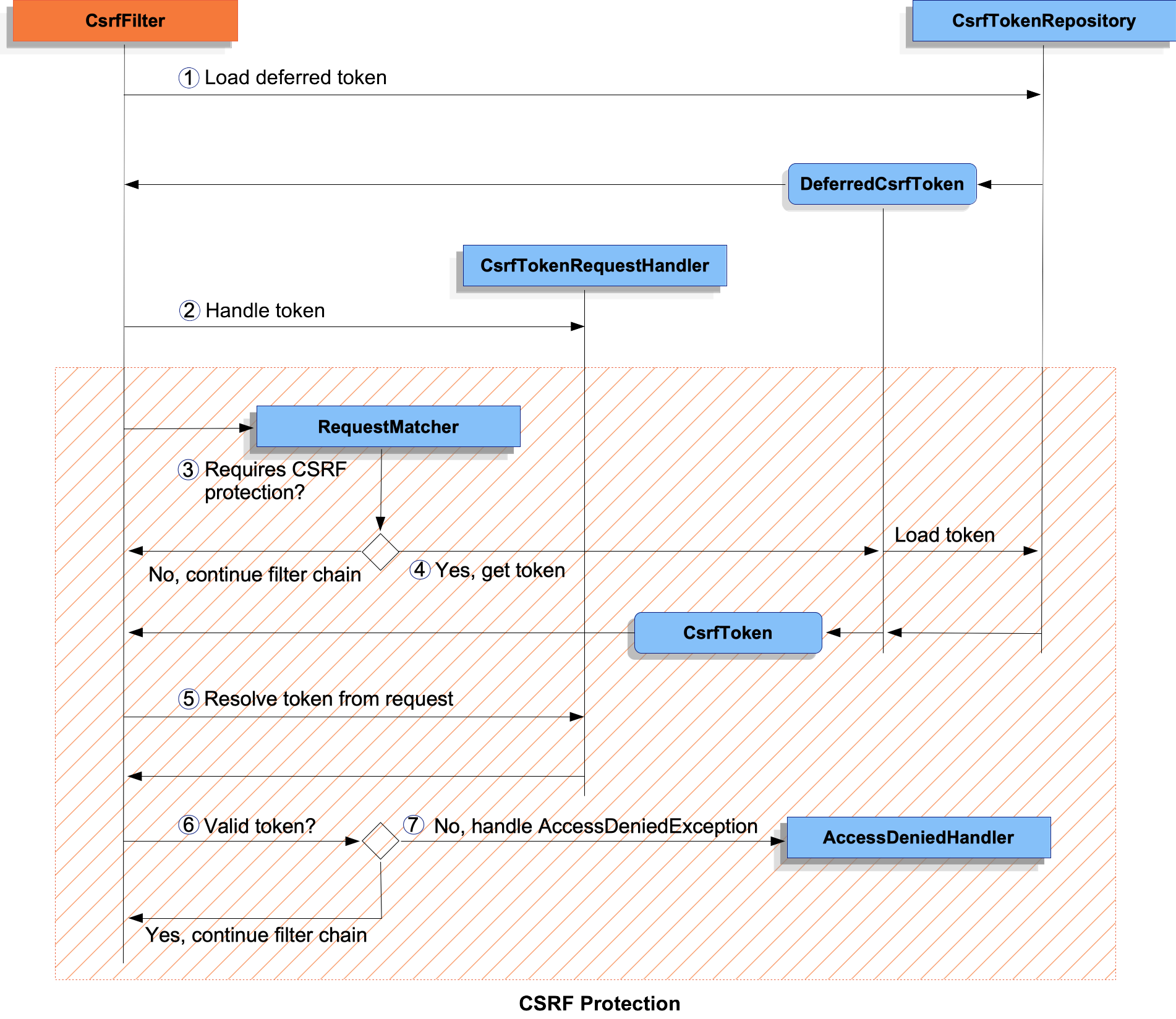
二進制
docs/modules/ROOT/assets/images/servlet/exploits/csrf.odg
二進制
docs/modules/ROOT/assets/images/servlet/exploits/csrf.png
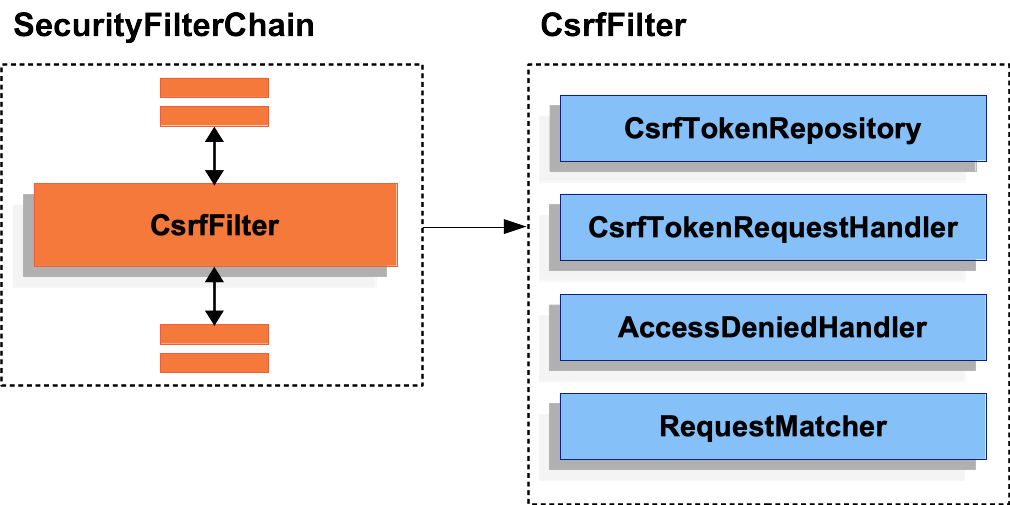
+ 1
- 1
docs/modules/ROOT/pages/servlet/authentication/logout.adoc
|
||
|
||
|
||
|
||
|
||
|
||
|
||
+ 1
- 1
docs/modules/ROOT/pages/servlet/authentication/passwords/form.adoc
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
文件差異過大導致無法顯示
+ 1104
- 39
docs/modules/ROOT/pages/servlet/exploits/csrf.adoc
+ 1
- 1
docs/modules/ROOT/pages/servlet/integrations/mvc.adoc
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
+ 1
- 1
docs/modules/ROOT/pages/servlet/integrations/websocket.adoc
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||